I just did, back in my previous post, when I wrote " For example, if a maintainer of a gateway plans replacement of that gateway, or maintenance, there could be a procedure that ensures that in those situations a second, perhaps temporary gateway is set up,"
I think that some of the readers here are not aware of how risk management works, or even what it is. Allow me to broadly paint a picture.
Risk management is fairly straight forward. First thing we need is a body of Governance (BOG). What’s that? Well, just a team that is responsible for the governance of our network. In practice: what they say goes and anybody that wants to be part of the TTN network MUST adhere to their decisions.
The BOG then stimulates and motivates the installation of what is called “an information security management system”. There are good standards available on what needs to be done, e.g. ISO27001. I know quite a bit about these standards, as you may have guessed by now  so if you have any questions about them, don’t hesitate, shoot.
so if you have any questions about them, don’t hesitate, shoot.
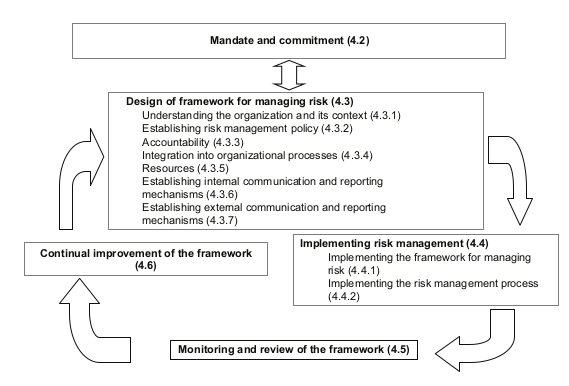
The ISMS is an implementation of a well known approach called “the Deming cycle”, which also is known as the PDCA (Plan-do-check-act) cycle. Actually, it’s nothing else than common sense: you plan to do something, then do it, check if results were as you hoped, if not you act upon it to correct the situation - and you use what you have learned to start a new iteration of the PDCA cycle (which involves a new context, as the times, they are a-changing…), ad infinitum.
Generally speaking,
- an ISMS starts with getting consent and sponsoring of the BOG, then
- doing an inventory of what assets there are (which is more than just technology, people matter for example),
- think about what risk levels are acceptable (and the BOG needs to agree here as they are responsible), then
- construct (and/or steal..) a list of threats,
- see if these threats work on vulnerabilities in your assets, then
- see what can be done about that (controls) to reduce the risk below acceptable levels, then
- implement these controls (mostly done in project form), then
- see if it all worked out as planned, if not: learn and correct.
And then it starts all over again.
It’s not something that can be done as a stand alone activity - if TTN would set up some kind of RA system (e.g. an ISMS) that requires that we ALL participate in it. We all need to be aware of the rules and adhere to them, we all need to consider risk and work with the comittee or group that is in charge of the ISMS.





 so if you have any questions about them, don’t hesitate, shoot.
so if you have any questions about them, don’t hesitate, shoot.