I’d like to get a TTN Gateway and put it in the loft of my office, where it will add a useful coverage area to the map. Are there any security implications to putting this device on my network connection?
Hmm quite a good question.
As for as I know there’s little security risk and it would as much depend on what gateway you use.
For the official TTN Gateway I don’t have one however don’t foresee any security risks. I don’t even think you require to portforward them either.
As for others (specifically Raspberry Pi) you have the usual security risks such as making sure you change default passwords and keeping them up to date and such.
Tl;dr: No more of a risk than other devices likely on the network.
I was thinking strictly of the TTN Gateway. A LoRA gateway is acting as a conveyor of public traffic via my cloud connection, which other devices don’t, at least explicitly, which is why I was concerned. I’d like to develop with LoRA nodes, so having a gateway within range would be helpful.
From the sense the traffic picked up by the gateway has very little processing done and is just forwarded to the network. The things gateway communicates over the more reliable and secure method too.
I suspect eventually there may be a method to attack networks via it but realistically its low risk. There’s likely more risk of other methods via external sources rather than a device that routes traffic.
I suspect that short term the biggest attack vector/risk is likely anyone in range of your Gateway’s WiFi signal. If I understand correctly TTN hasn’t yet released option to turn off/disable (I’m using Wired eNet not WiFi)…given functionality/reliability issues that are well reported I guess their focus is on getting things working vs turning things off! 
if in doubt put GW on separate back-haul connection or at least move it out into a DMZ (and still behind a firewall?!) You may need to place on same network for config if not using WiFi, but it can be pushed out once configured.
Given the choice I’d rather connect by cable and turn off any WiFi connectivity, if this were an option. You are clearly more au fait with networking I.T. than I am, I was hoping just to plug it in an focus on getting end nodes working.
and you can … I see maybe 20 wifi ssid’s… secured… no problem.
if you want a TTN router you can cable connect it and wait for the update where you can switch off wifi completely, or you buy another gateway.
but to me imho there’s no problem at all at this moment … I have to see the first POC to misuse the TTN gw over wifi
Wi-Fi security is continually evolving, just because something ‘claims’ secure doesn’t mean it is truly so :- …what was once considered secure is no longer so and also in any given system implementation there may be weaknesses or poor implementations. As you know we now rarely uses WEP, WPA has moved on, WPA-2 saw issues late last year and early this and many router and even GW manufacturers have issued new firmware to address some of the issues(*). Given the problems TTP (and its subbies) have had getting LoRa subsystem or even full GW to function 100% reliably are you confident there are no Wi-Fi related issues?!
…what was once considered secure is no longer so and also in any given system implementation there may be weaknesses or poor implementations. As you know we now rarely uses WEP, WPA has moved on, WPA-2 saw issues late last year and early this and many router and even GW manufacturers have issued new firmware to address some of the issues(*). Given the problems TTP (and its subbies) have had getting LoRa subsystem or even full GW to function 100% reliably are you confident there are no Wi-Fi related issues?! 
As you will also know the new WPA3 spec has just been released to continue to evolve security…hence my suggestion that Wi-Fi likely a large potential attack vector…basic premise for anyone concerned with network security is if you don’t need a n/w interface turn it off/disable if in doubt…only with the TTN GW you cant…or can you?
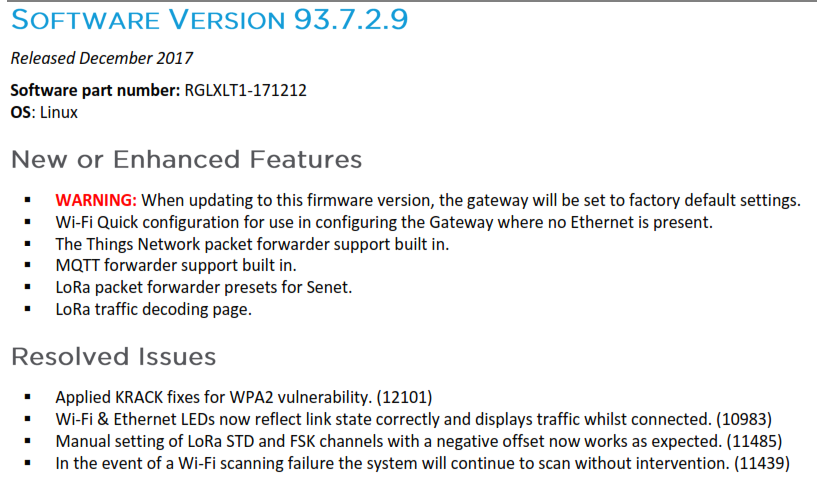
(*) e.g. Laird issued this update in December to address WPA-2 KRACK vulnerability:-
are you confident that every device on your LAN is 100 % secure ? now and in the future ?
I’d also say what I’d call the “windows” effect applies.
For computers you don’t see as many viruses, malware and such for OSX & Linux systems because the majority of people don’t use them. And that’s why windows is the most commonly affected.
I don’t know many hackers that will try and target LoRa gateways to get into your network compared to Smart TVs, TV Boxes, Phones, Smart hubs & speakers, Printers and more. As you’re in the UK I’d say its more likely that there’s going to be a issue with your Router Modem Combo being more of a vulnerability than a LoRa gateway.
So lets be real… how would you attack a system like this ?
I bet my money on the ‘auto update’ firmware as weakest point … but even that would not be easy
I think the question would be what are we also hacking for? To get access to the owners personal network for files or to get the gateway under their control?
In the 3 years my gateway has been up, firstly as a private LoRaWAN network then as part of TTN I’ve not seen any issues. It doesnt use wifi so unless you are part of the TTN community you wont even know it is there.
The real question isn’t really if somebody can take over a gateway or not, but if the gateway can be used as an attack vector into the office network…
Easiest is to isolate the gateway in a separate network, that way whatever happens won’t affect your business.
Network isolation can easily be achieved with a somewhat decent router, or even with Steve Gibson’s “3 dumb routers”…
(I do agree that the gateway is a a very low risk device compared to other appliances, but if it is about a corporate network, better be safe than sorry)
I would guess most likely as an entry point to the network - most likely via a GW rather than a simple low compute power/low data connection sensor node - so you can then look for ‘easier’ to hack/control devices for e.g. botnet building.
Sadly IoT security is increasingly seen as an issue and we have already had examples of large botnet & DDoS attacks & ransom/extortion efforts as a result (esp using laxly managed or configured ‘consumer’ IoT devices - IP CCTV cameras, ‘smart’ TV’s etc)…IMHO we need to be mindful from the start (not least as once deployed ‘fixing’ issues could be a real PITA  Most of the devices and data collected on a LoRa network, under TTN are a ‘dont care’ wrt other people seeing the data but then there is always the exception and so you need to protect for all.
Most of the devices and data collected on a LoRa network, under TTN are a ‘dont care’ wrt other people seeing the data but then there is always the exception and so you need to protect for all.
We also have a responsibility to the rest of the TTN and wider LoRaWAN using communities as it will only take one or two bad headlines around the world about ‘TTN used to launch major bank/credit card take down in DDoS attack’, or ‘TTN used to phish personal details from 85 year old grannies and steal their life saving’! or some such to cause people to question and loose faith in the technology making our deployment efforts harder… 
‘Professional/corporate’ devices struggle with security at times, and I would suspect that amateur/hacker-space/community built devices will likely vary even more wildly in care/security of builds (not a criticism folks just a fact of life wrt varied skill sets and available tools/resources for testing!), and I know many are using linux and there is often assumption of Linux or MAC more secure than WIndoz but you only have to look at recent Gentoo Linux snafu wrt Github to see how easy compromises may slip through…as for myself I assume none of my kit is 100% secure and simply try to mitigate within reason without paranoia 
Some useful thoughts, thanks. I’ll be at a meeting of the TTN Norfolk (UK) group on Monday and will mention this discussion.
@Alexmouse: Applause for thinking about security from the outset.
I’m with @Jeff-UK on this one - always choose the most secure option from the start. As a minimum I would place the GW on your router’s DMZ. To “disable” WiFi I would guess you can simply enter erroneous information?
Just because we can’t see why someone would want to hack a GW doesn’t mean it won’t be hacked - we’re not talking about individuals doing manual hacking anymore, there are automated systems constantly looking for vulnerable devices, so it’s not a case of “if” but “when”.
Usually isn’t the DMZ Feature where it essentially opens up all ports to the device? Of which that’ would make it a greater security risk than being behind the built in firewalls and such.
I’m guessing you mean isolation? Of which I’m not sure how many commercial routers support this. While some things call this DMZ most routers still allow the device to access other devices on the network.
However an idea is, if actually using the wi-fi you could create a guest network of which most UK ISP’s hubs support and that would provide as good isolation.
DMZ
So indeed, it would actually open the gateway up to more risks as the gateway itself doesn’t run a firewall.
Obviously it also depends on what the “router” is most people use. In the UK we’re pretty much forced to use the one the ISP Supplies and in a best case then connect a third party one to it.
However it does look like using a guest wi-fi network could be an option. You have the wireless security factor then however most of the routers that come with ISPs isolate these better than “DMZ” which just opens all traffic up.