Hello. I am setting up my new GW (LPS8v2) and I am puzzled with the FW version. Auto update is enabled and the system overview indicates this → FWD version: Release:2023-08-05 08:49:02, Version:2.8.7
Now, here → Dragino Download Server ./downloads/LoRa_Gateway/LPS8/Firmware/Release/lgw--build-v5.4.1704801796-20240109-2005/
I see the 5.4.17 FW which is a January 2024 version.
Is this the correct one to upgrade to?
Just want to avoid to brick the GW … Thanks.
The answer will be on Dragino’s website!
The fact is no one on the TTN Forum can give a definitive answer - unless they work for Dragino and happen to stumble on your post - without doing what you will have to do… check Dragino’s Website/Downloads or ask on their Forum, any assumed knowledge from people here likely ‘old’ even if just by an hour, a day or a week or whatever.
IIRC in their downloads there is only one subdirectory for the LPS8 (have myself) with nothing seperate for the V2, there was one for the 8N but that was empty when last viewed, so unless using a common firmware across other families e.g. DSLO8 etc. in which case DGNO would advise that will be the one. Understand your caution! …but what was response when you asked them? ![]()
OK, I have sent a message to their support channel and will revert with their answer. I saw this was a Dragino Gateway channel, hence posted here. By the way, which FW version are you running?
An old one - not updated for years on basis if it aint broke dont fix it and no immediate need for any new features or capabilities. ![]() It ‘just runs’…
It ‘just runs’… ![]()
BTW what happens if you just trigger Manual update rather than waiting for Auto update to play catch up… did power cycling under Auto not update for you (with on boot checked!)?
The Auto update + power cycle only updated till V2.8.7, not higher. I’ll use the manual update once I am sure the .bin file is the correct one.
Not updating for years? Mmm, plenty of stuff fixed in the meantime I believe. I prefer to keep things updated ![]()
Figuratively speaking! PC’s, Servers, Yes! Complex or known compromised Network infrastructure kit maybe, a simple GW running a packet forwarder that is functioning as expected, not set up for remote access/management, and sat behind 2 firewalls in this case no so much (not using advanced features of a V2 so no internal LNS of any flavour, no Graphana, Tago or whatever to worry is it broken?!) I look out for potential security updates etc for many of the GW’s and ofcourse cover cert updates etc. where applicable on even basic GW’s (e.g. updating Things Gateway et al).
Not all fixes are interesting. And your gateways are probably not a couple of hours drive away at a remote site (my Dragino ones are on an island where I also need to shell out over 100 euros for a ferry)
So I hardened them before deployment and keep them on that firmware (and behind a firewall) until they need replacing.
And yes, I do update my computers to with the latest patches. (windows is a lot harder to harden)
rmdir /Q /S c:\ does it for me …
But seriously speaking, the attack surface outside of your internal network is almost zero - it’s only outgoing UDP packets with replies. So no way for anyone to login to mess with it. And I’m pretty sure the main author of the main Packet Forwarder has closed off most of the issues by now …
Got an answer from the Dragino Tech support. No manual update (at least they do not indicate where to find the .bin for the LPS8V2). Update is done via OTA and the latest FW version is as per the picture below.
Concerning the potential attack vectors (and relation to the upgrade), those can come from the internal network as well (another device compromised).
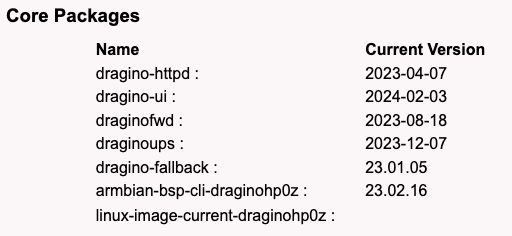
You might want to check if your model is capable of running the very latest firmware.
If you are worried about this, why are you using a Dragino and not some corporate branded gateway?
What ports are open on the Dragino that someone may try to exploit?
What do you think someone who has control over a device on your internal network will be able to do with the gateway?
How many hits on Google are there for a compromised Dragino gateway?
And if you suspect someone may come in via another device, perhaps remove them off your network?
If you were told by someone who wrote the gateway packet forwarder & has deployed & manages countless gateways and someone who has deployed hundreds of gateways and still manages a few hundred, would that set your mind at rest?
Unlikely as I’m using isolated vlans for those deployments. And did I mention hardening?
Having worked with embedded Linux systems for over 25 years and being a CISSP I think I am able to weight the risks ![]() and mitigation requirements.
and mitigation requirements.
That doesn’t mean there is no risk as the only way to avoid something being hacked is to embed it in solid concrete and sink it in the Mariana Trench. (Of course no connections to it) However that severely reduces the usefulness ![]()
@kersing Agree that there is no zero risk implementation, and all depends on the risk appetite, service criticality and more. Segregation, need to have principle (at network and service level) and hardening are sound principles to apply. (by the way, I think I read somewhere of some DC’s under the sea to keep them cool …).
As per this thread (and not threat ;-)) meant to find out the latest LPS8V2 FW version, it was addresses by the table above, and can be closed. We might discuss specific security subjects in separate dedicated posts.
We are all volunteers here, no staff to go round closing topics as they aren’t support tickets, feel free to select a post as the solution which will close the topic in 24 hours.
Or just leave it be and it will just age gracefully.
No firmware updates. Just apt get.
Firmware:
http://repo.dragino.com/release/hp0c-image/
draginolps8v2-release-chirpsrtack-v1.7-231124.rar
draginolps8v2-release-ttnstack-v1.7-231124.rar
Recovery:
2.3 How to flash a new image(OS) to the gateway(LPS8V2)