Finally I set up my DIY gateway (Basel, Switzerland) and fund this strange packet received by it:
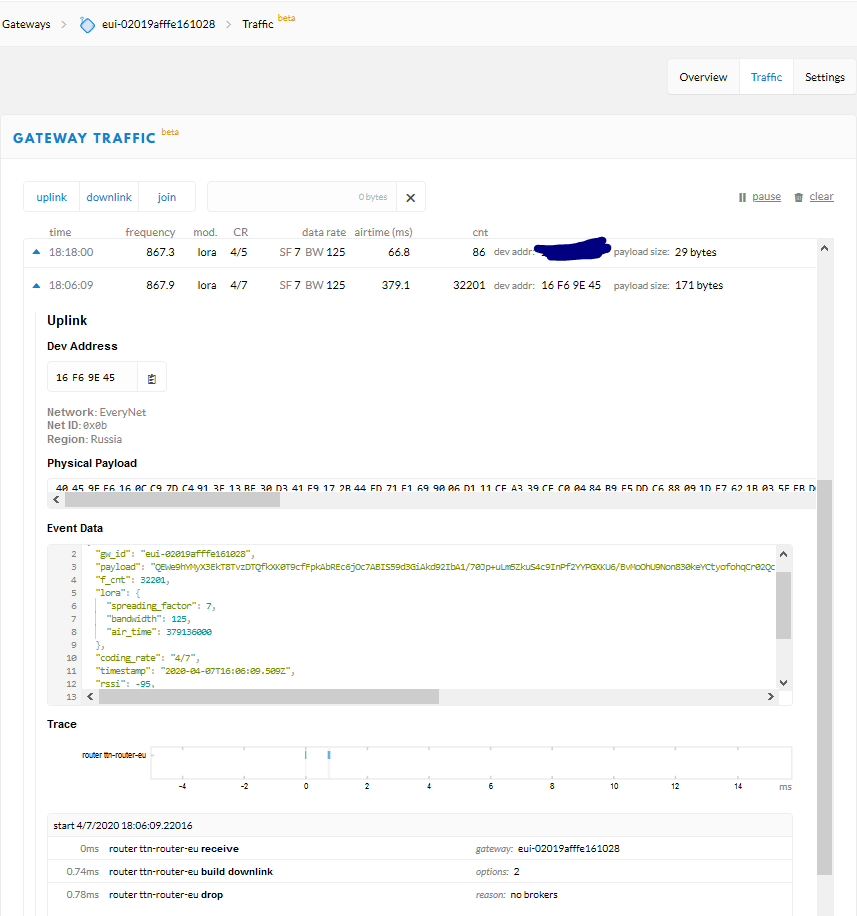
Is it possible this transmission came from Russia/EveryNet or it’s rather an invalid network id?
Can the 379 ms air time be somehow used to calculate the possible distance of the node ? (SF7 BW125)
If you search the forum you will find several such instances (had quite a few myself). This says where service is located but devices can end up in many places globally. E.g. if device is a logistics/asset tracker (e.g. on a lorry, a container, piece of plant /equipment, or even a pallet of goods or a carried by a person. etc) it could well come into your local environment and be picked up on your gw. Wether the payload gets back to target back end will then depend on if they have deployed associated gw infrastructure in your area or if they have a roaming agreement with any service provider who have deployed local GW’s or if they are using e.g. PacketBroker etc.
Also, the total packet being a whopping 171 bytes might indicate it’s not LoRaWAN at all. TTN cannot tell for sure as it’s not a packet for a device it knows, so it cannot validate the MIC. Still, TTN shows some debug information, boldly assuming it’s LoRaWAN and hence boldly interpreting some specific bytes that, in LoRaWAN, are not encrypted and have some specific meaning.
So, it might very well be a LoRa device using a different protocol (and the same sync word, or the sync word was not filtered out)?
Aside: I assume your gateway is not forwarding packets that have an invalid CRC?
Thanks for the explanation!
Good catch - I temporarily enabled forwarding noCRC packets to debug the forwarder and forgot to turn disable it. Will do it straight away. ![]()